0Tolerance is a listed Payment Card Industry (PCI) Qualified Security Assessor (QSA) and can help you understand the PCI Penetration Testing requirements.
PCI Penetration Testing Requirements
The PCI Data Security Standard (PCI DSS) is a contractual requirement set forth by the PCI Security Standards Council (PCI SSC) to protect cardholder data. It applies to any organization that stores, processes, or transmits cardholder data, regardless of the size or number of transactions. It also applies to organizations that impact the security of card transactions. The PCI DSS protects cardholder data by requiring organizations to implement security controls and best practices. Level 1 organizations must undergo annual third-party Qualified Security Assessor (QSA) audits to ensure that their security controls are effective and comply with the PCI DSS. Requirement 11.3 of PCI DSS version 3.2.1 and 11.4 of PCI DSS Version 4.0 detail penetration testing requirements.
PCI Penetration Testing Rules
Must be performed by a qualified resource, free of conflict of interest with the organization.
Who needs it?
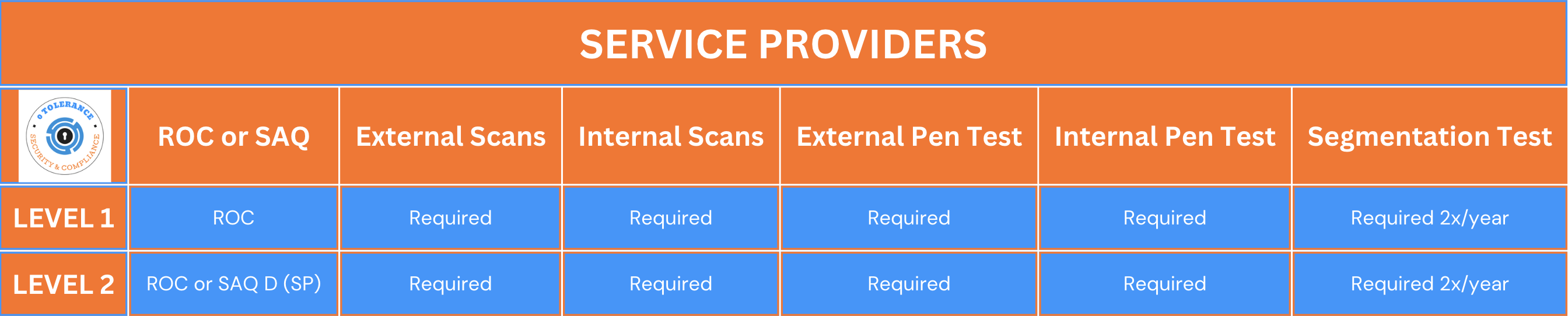
- All Service Providers must undergo a full annual pen test.
- All Service Providers must undergo a second annual pen test for segmentation testing purposes (6 months from the full test).
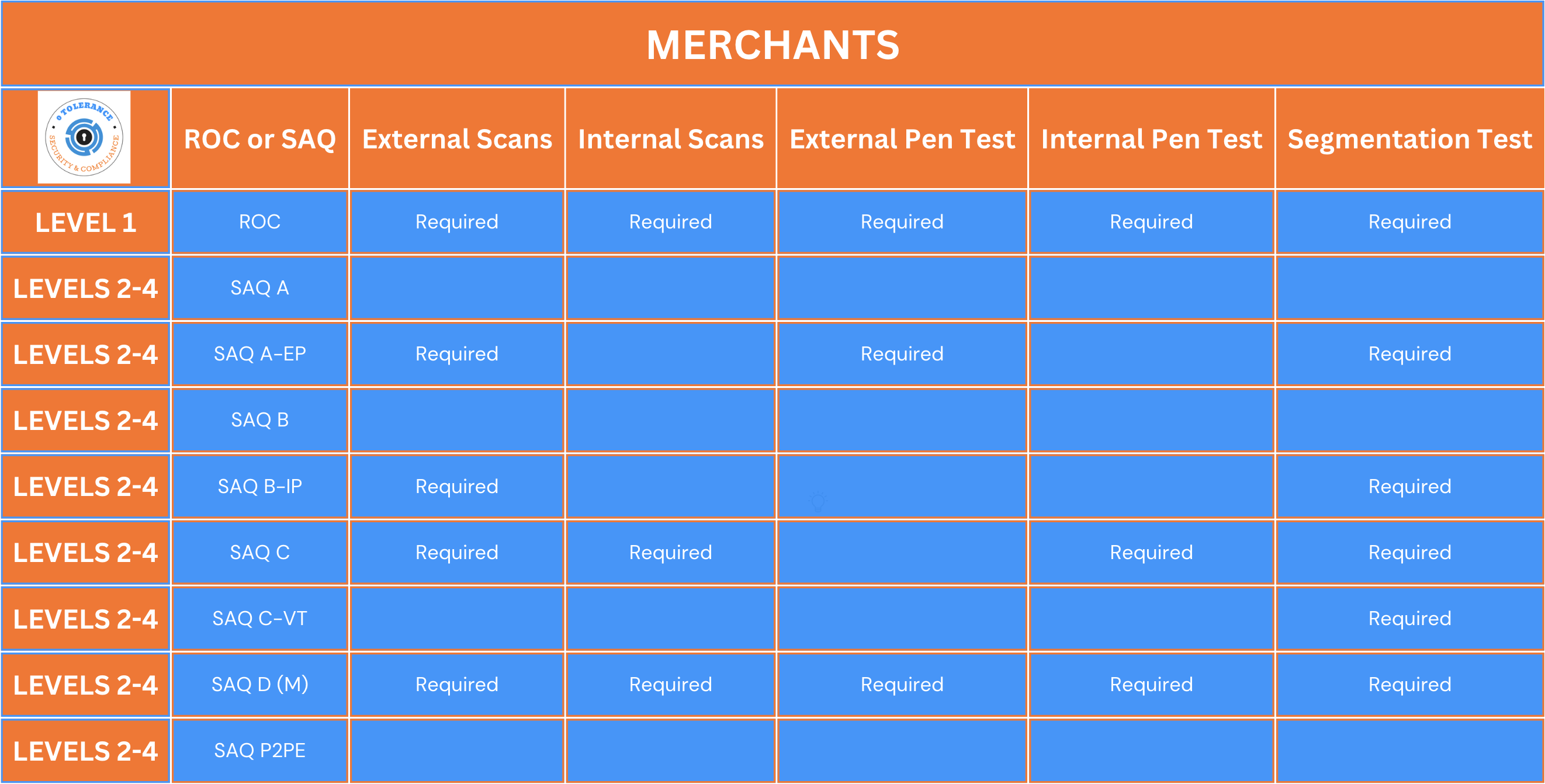
- Level 1 Merchants must undergo a full annual pen test.
- Level 2-4 Merchants completing SAQ Type A-EP must undergo external network penetration and internal network segmentation testing.
- Level 2-4 Merchants completing SAQ Type B-IP must undergo internal network segmentation testing.
- Level 2-4 Merchants completing SAQ Type C must undergo internal network segmentation testing.
- Level 2-4 Merchants completing SAQ Type C-VT must undergo internal network segmentation testing.
- Level 2-4 Merchants completing SAQ Type D must undergo external network pen testing, full internal network pen testing, and internal network segmentation testing.
► Level 1 Compliance Assessments (Report on Compliance)
► Level 2 Compliance Assessments (Assisted SAQ)
► Gap, Risk and Readiness Assessments
► External network and application pen testing
► Internal network pen testing
►Segmentation testing
► External vulnerability scans for ASV purposes
► Attestations of Scan Compliance (AoSC) and Seals
► Complete the Self-Assessment Questionnaire(s) Online




